
Close Window
StealthSurfer Flash Drive
| Author: | Artiom Bell |
| Date: | 2008.03.27 |
| Topic: | Security |
| Provider: | Stealth Surfer |
| Manufacturer: | Stealth Surfer |

| Author: | Artiom Bell |
| Date: | 2008.03.27 |
| Topic: | Security |
| Provider: | Stealth Surfer |
| Manufacturer: | Stealth Surfer |

When using a public computer, have you ever wondered if the person that will be using it after you might steal your password, have access to your data, or be able to see your internet history? Well, wonder no more because StealSurfer software was designed just for that! StealthSurfer is portable security software that comes installed on a flash drive which you can take anywhere you go. Pop the flash drive into one of the USB ports on the computer that you are going to be using, a few clicks, and you are ready to send e-mails, surf the web, and even use your own programs.
All of the StealthSurfer drives include the same software and the price is soley determined by the size of the flash drive. Essentially you will have the same functionality with the cheapest one as you do with the most expensive one; however, if you are planning on instlling additional software such as office or any other software of your choice, flash drvive space could potentially become a problem if a small drive was purchased.
 |
$179 |
 |
$205 |
 |
$279 |
 |
$339 |
The installation which was more like registration was fairly simple. Enter personal information, log-in information for the server based software along with the licensing key and you are ready to go.
The first time you start, the process will take a few extra minutes, so grab cup of coffee as you fantasize about your new security features. An alert screen will pop up telling you to wait. As we said, the first time will take slightly longer, but in our consecutive tests there were no issues at startup and MojoPac initialized smoothly.
In short, MojoPac is Windows to go. The reason MojoPac is so portable is because of the fact the once the StealthSurfer is plugged in all that you have to do is press "Run MojoPac", enter your username and password, and you are taken to the Mojo Desktop. This procedure closely resembles logging into windows, you enter your user name and password and you are in. What makes MojoPac great is that this type of simplicity is carried into creating this software. Quite frankly the 3-page manual that was included with the USB drive was not necessary to operate this program, the user friendly, on-screen instructions were all that was required to correctly registering this software..
 |
 |
 |
 |
The first thing that I noticed after registering this software was the start button. The makers of MojoPac have done a excellent of making this environment to resemble Windows environment by including all standard features of Windows XP. All accessories and games come included. The operating desktop is also modifiable and comes with backgrounds that can be selected much like in the Windows XP.
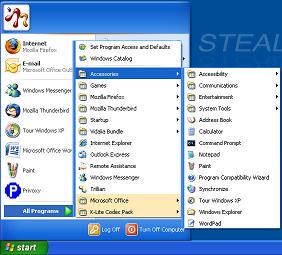 |
 |

The next thing that I noted while browsing the Mojo Desktop was the "My Computer" folder. If you look in the picture, you can see that the main drive of this operating system is not "Local Disk C" or you other onboard hard drives; it is, in fact, "Rally 2". When you are using the Mojo Desktop, you are completely isolated from the host system. This in itself is a great security feature and one of the more important ones. The isolation implies that any operation such as surfing the web, chatting, typing is not recorded on the host system.
To test this I decided to use key logger programs. In general, key loggers are programs that used to record keyboard keystrokes. Key loggers also have the ability of recording which programs are opened as well as taking screen shots at set intervals. The majority of key loggers also have the ability hide themselves from the users making them virtually undetectable thus making them a considerable security thereat. Be happy that MojoPac render key loggers ineffective. All the key loggers that were tested were unable to detect keystrokes while running Mojo Desktop.
The following key loggers were used:
Following the reasoning behind a portable computing environment, a couple of programs used by everyday people to see if they can actually run.
The following programs were installed:
No problems were encountered during the installation of these programs as well as while running them. Watching videos was also not a problem.
Hushmail is a program that works very much the same way as AIM or MSN Message except that all of its functions are completely encrypted to protect your privacy. If you don't want anyone looking at your conversations then Hushmail is the way to go. It is a little tricky starting a hushmail account since it requires more steps than setting up the MojoPac.
After setting MojoPac direct your attention towards this icon:

It is a rather important icon containing more instructions concerning the creation of Hushmail and information about the your StealthSurfer. You will be forwarded to the StealthSurfer Start up page on which you will have to click the Hushmail link. Stealth Surfer already comes with Hushmail, however you will have to create your own account.

 |
 |
You will have to first create your Hushmail account and then upgrade it using the MojoPac key that came with the package. The ease of set-up carries over to the creation of the Hushmail account.
Hushmail is dedicated to privacy which makes this a perfect companion to the rest of the StelathSurfer software. Their standard 2048 bit encryption exceeds that of the standard email 128-bit log in encryption certificates. Hushmail not only encrypts during the log in process but stays encrypted through out the whole session. Furthermore, because you are entitled to a Premium Hushmail account, you get 250 MB of storage space which is of course also encrypted. If you have sensitive information that you don't want others to know about, Hushmail is the way to go.
Another neat feature about the Hushmail system is that you also get the Husmail messenger. Messenger also offers standard encryption which is perfect if you are going to use it on your job or any other place where internet access is monitored.

The messenger is not as graphically intense as the other chat clients such as Trillian, MSN Messenger, or AIM; however, all of the functionalities are there of a standard chatting client are there. It is no wonder that there were no option to use video chatting since that will most likely not be allowed by the high encryption protocol that Hushmail client is using. The benefits of encryption also increase if the party you are communicating with also uses Hushmail.
If you have ever bought more than one thing online, or just have multiple email accounts then you probably know how annoying it is to type in your user id and password or your billing information over and over again. Roboform has been created just the purposes of filling out your information. Roboform saves the passwords and other types of information into what they call passcards. The passcards are then stored under a specific identity, therefore multiple identities can use the same program without interfering with each other or revealing password information like the browsers do.


 |
Roboform is an excellent program that fits well with the rest of the StealthSurfer software. While it allows the user to save time by filling out information, it does not compromise the security side of the stealth surfer. All the passcards and identities are protected by their own master password and therefore are kept separate from each other and are completely confidential. Roboform is resets every time you click "Log off" and auto resets after a number of minutes that is set by the user. The installation of Roboform is quite easy, on the same page startup page that you downloaded the Hushmail, you can locate a direct download link to download Roboform. Please note that you will have to return to the same start page and click the activation link in order to activate Roboform. Once installed, Roboform is more or less self explanatory. First you would need to create and identity, under which you would build you passcard. It will constrain everything about you including your address, phone numbers, credit cards and will auto fill that information as requested by the web page.
Tor is a security program that comes pre installed into Mojo. It works as a client that connects to the net of different random servers across the world. The program call this chain of connections a circuit. Once the circuit is established, any transmission that you sent will be bounced off diffent servers therefore anyone that tries to intersect your connection will not really know what it is used for, or where it is going. Here is a map of all of the server around the world which could portentially be used to bounce your signal. Tor will chose a random amount of random servers and use them to redirect your traffic through them.
The control pannel
The user has the ability to eneable or disable Tor without using the control pannel then just by clickng the lower right corener on the Firefox browser that came with StealthSurfer.


There are several issues with this software that have to be noted. These issues may or may not be important depending on the situations the users are presented with while using StealthSurfer. Here is a list of problems that were encountered:
Issues with MojoPac
1. Doesn't work on Windows Vista, Linux, or Mac OS. If you just happen to need to use your StealthSurfer on Vista, you will be presented with and rather displeasing messages telling you that you are unable to run it.
2. Administrative Control issue:
3. Tor Message logs. Aside from being hilarious when a security software that tells you that it is not secure, this might be a real problem for some users.
4. If you happen to be on the network on which the administrator limited the ports that can be used to connect to the internet, it will be impossible for you to use Tor. As can be seen to the screen shot when you are sitting on the limited network, Tor doesn't have the ability to communicate with the outside world. The ports can be changed in the Control Panel; however, if the administrator decided to block all of the ports, then it's tough luck trying to find a viable port.
5. Because of its nature, the performance of StealthSurfer largely depends on the environment and the system you are running it in. Naturally the more powerful the system the less problems you will have while running this software.
| System 1 | System 2 | System 3 |
|
|---|---|---|---|
| Processor | Intel Pentium 4 |
Intel Pentium M |
Core 2 Duo |
| Processor Speed | 2.8 GHZ |
1.7 GHZ |
|
| RAM | 1.0 GB |
512 MB |
2 GB |
Memory problems were encountered while running StealthSurfer with 512 MB of
system. On System 1, for some unknown reason Mozila Firefox would a consume most of the processor doing absolutely nothing.
This software largely depends on the user and what it will be used for. On one hand, it could be very handy to have your own mini-PC on your flash drive with excellent security features. On the other hand this software might be useless for you. The overall impression of this software demonstrates that the creators put forth much effort to compile and create the whole system like environment. If you plan on purchasing this software, place great consideration on where and how it's going to be used.